With the Internet and mobile Internet booming to become almost ubiquitous, all aspects of people's daily life are also showing a deep integration of online and offline.
Regardless of the many online and offline services, the objects of their services are people. How to determine a person’s identity quickly, accurately, safely, and efficiently, so as to quickly link personalized services, is an important area that has been improving in the field of identity recognition from the past to the present and the future.
Traditional identity authentication is based on various documents. With the rise of the Internet and smart phones, the identity authentication industry has developed various electronic-based identity recognition and authentication schemes. Such as SMS authentication code, dynamic port token, USBKEY of various interfaces, various ID cards, etc., as well as fingerprint authentication, face recognition, iris recognition and so on that have emerged in recent years.
But no matter which scheme is adopted, the following elements are satisfied to varying degrees:
1. A unique identification with a characterizable identity (such as passwords, various personalized hardware, personal biometrics)
2. Can distinguish whether the unique identifier is legally used (usually protected by a password)
These solutions are like giving each person who needs to be identified with a dedicated online key. Different solutions have different strengths in terms of the uniqueness of the key and the use of unique identification.
1. The core issues of identity authentication:
The core issue in identity authentication-the strength of uniqueness. All the problems of identity authentication can be boiled down to two problems:
(1) How to distinguish an individual from other individuals is to give the individual uniqueness.
(2) How to present the result completely and credibly. That is to convey the uniqueness of the individual.
Examining many programs, it is not so.
For example, ID documents such as ID cards, passports, Hong Kong and Macao passes, etc., give individuals a unique expression from the number, and use anti-counterfeiting technology and chip technology to protect and transmit this uniqueness.
For example, a dynamic pass token is issued to an individual to be bound to his identity, and the currently generated dynamic password is input when needed to confirm that the user owns the token, so as to convey the uniqueness of the user.
Such as USBKEY of various interfaces. A unique certificate is given to an individual through a digital certificate, and the uniqueness of the individual is transmitted through the digital signature with the bound private key.
Take fingerprints, for example, by collecting personal biological characteristics and forming characteristic values through fingerprint algorithms to distinguish them from other people’s fingerprint characteristic values to form uniqueness.
It is found that most of the technical investment is to solve the strength problem of "uniqueness". People continue to improve their technical level, upgrade algorithms, and increase the length of keys. The fundamental reason is to protect or enhance the strength of "uniqueness".
2. Cognition of unique strength and its classification
However, due to the lack of quantitative evaluation and understanding of the "strength of uniqueness", people usually ignore the core issue of "uniqueness" in the evaluation of different programs. In fact, although the definition of "strength" lacks a unified standard, it is not that complicated. For example, we can define the strength of uniqueness as follows:
The first level: has a unique number that is disclosed, such as an ID number, two-dimensional code, etc., which only has an identification function. No protection for uniqueness.
Second level: On the basis of the first level, password protection is added. Such as static password, or SMS verification code. However, since static passwords need to be preserved, there are time problems with clear codes, and their reproducibility is relatively high.
The third level: on the basis of the second level, add a password generator (such as a dynamic token). A one-time password is generated temporarily through hardware to protect the right to use the ID number. The password does not need to be stored in plain text, and it is used for one time. Compared with the second level, its uniqueness strength is further improved.
The fourth level: On the basis of the third level, ciphertext is generated through intelligent hardware to interact. The strength of uniqueness at this level has been greatly enhanced. At this stage, it can be considered one of the highest strengths of uniqueness.
At present, most of the identity authentication schemes are between the first level to the fourth level. But obviously, even the uniqueness scheme of the fourth level still has certain risks. The risks are:
1. The ciphertext scheme is based on mathematical problems. If the math puzzle is broken, the intensity will decrease significantly.
2. Although the key (such as the private key in USBKYE) is not readable, it is statically stored in the USBKEY memory. There is a risk of leakage.
It is for these reasons that people need to continuously upgrade technology to protect the security of keys.
On the basis of mathematics, Fudan Microelectronics has proposed a unique solution by adding quantum properties in physics. This solution is mainly realized by providing an NFC identity that cannot be copied. It is mainly based on a technology called "Physical Unclonable Function", also known as PUF (Physical Unclonable Function).
3. Introduction of PUF technology
Fudan Microelectronics applies PUF technology to the field of NFC certification. In short, the characteristics of this technology are:
Uniqueness that cannot be replicated.
The so-called cannot be copied, including:
Chip designers (such as Fudan Microelectronics, the chip designer) cannot copy
Chip manufacturers (such as manufacturers that produce chips) cannot copy
The unique identification manufacturer (such as the certificate manufacturer) cannot be copied
Owner units (such as financial institutions, government agencies) and users cannot copy

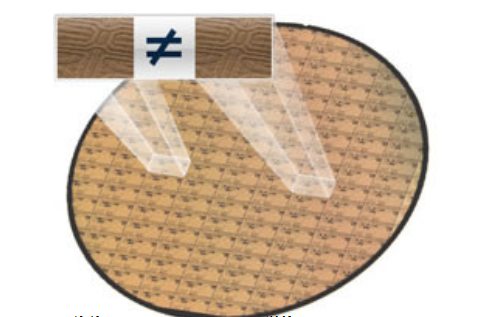
Use the extracted chip "characteristic" information instead of simply using the key stored in the chip's storage area. In this way, the physical uniqueness and randomness of the key are guaranteed, and the chip is given a strong ability to resist attacks.
(2) The natural randomness that does not require a random number generator.
(3) The data realized by PUF is different every time it is temporarily generated, and it disappears after use. Therefore, PUF data can hardly be attacked by outsiders.
4. Unique Issuance and Authentication Service (UIVS)
In order to allow PUF NFC technology to be conveniently used by enterprises, Fudan Microelectronics provides unique issuance and certification services (UIVS: Uniqueness Issuance and Validation Services) to realize the key issuance and encryption and decryption of a full set of PUF NFC encryption and decryption chips. Authenticity verification function. Fudan Microelectronics' business based on the UIVS cloud service has provided a wealth of successful cases and mature solutions in various fields such as item uniqueness, animal uniqueness, and identity uniqueness. Including white wine (national Taiwan wine, Moutai wine, lotus wine, etc.), red wine, foreign wine, medicine, identification certificate, hand-made toys, cosmetics, purple clay pot, calligraphy and painting, mahogany furniture, etc.
1. KMS system (key management system)
2. Issuing system
3. PUF database management module
4. Authentication system
5. Trusted delivery
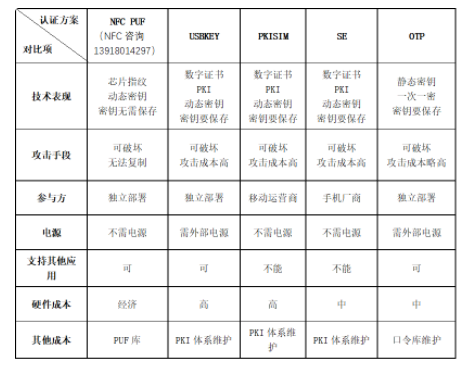
V. Comparison of identity authentication schemes
The following table lists the comparison of several mainstream identity authentication schemes based on unique hardware: